Win32/Wacapew.C!ml is one of the most annoying viruses that drops multiple malicious files on various folders in your computer system. The primary intent of this virus is to damage your computer and steal personal information. So, you need to remove it immediately after you notice it on your computer.
If you want to remove this virus without digging into manual malware removal methods, then you should consider the Spy Hunter software. This antivirus detects and removes malware from your PC automatically. It will also ensure they never return. Continue reading to learn more about removing Win32/Wacapew.C!ml.
Is Win32/Wacapew.C!ml Malware or False Positive?
Yes, Win32/Wacapew.C!ml is malware and is classified under Trojan Horse. If your antivirus picks up this virus, it means your computer, user’s files, and personal information are at risk. This virus can block you from accessing your computer files and also cause several damages to your PC. Some of these damages include
- Dropping malicious files in your PC’s folders.
- Steal multiple confidential and personal information from your PC.
- Download other threats into your computer.
- Leaves a backdoor for remote hackers to access and take control of your computer.
Automatic Way to Erase Win32/Wacapew.C!ml
There are multiple antiviruses online that promise to detect and remove viruses. However, these antiviruses, especially the free ones, only detect viruses. They can’t remove them completely. Spy Hunter, on the other hand, is the most reliable antivirus that will detect and remove the Win32/Wacapew.C!ml malware from your computer.
Spy Hunter was developed using an updated database. The developers of this database also update it regularly to detect and eliminate newer threats. This makes Spy Hunter the best antivirus to remove this virus from your PC. Use these simple steps to download, install and run the Spy Hunter software.
Step 1: Using this link, download the Spy Hunter software. Then, open it from your download history.
Step 2: You will see a User Account Control icon on your screen. Select “Yes” to proceed with the installation.
Step 3: Select the language you prefer and click on Continue.
Step 4: Accept both the Privacy Policy and End User License Agreement and click on Install.
Step 5: After installing, click on the Finish icon. You will then have to add your information or accept the default information.
Step 6: Search for Spy Hunter on your homepage’s search bar. Then, open it.
Step 7: Choose Start Scan Now and Spy Hunter will locate all the viruses on your PC automatically.
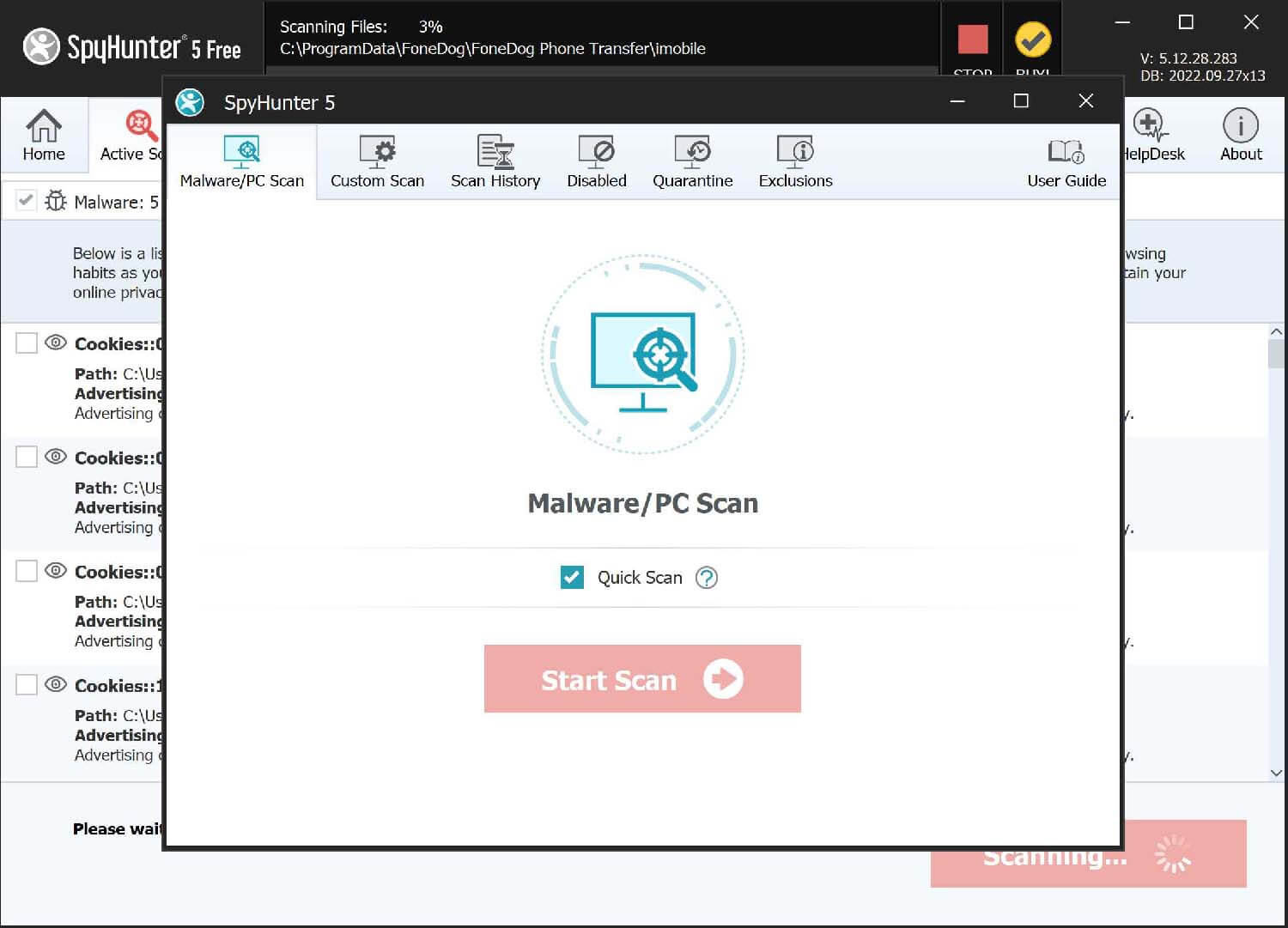
Step 8: After Spy Hunter has completed its scan, it will expose the viruses on your computer, including Win32/Wacapew.C!ml. Finally, click on the Delete button to remove all of them.
The Most Advanced Guide to Remove Win32/Wacapew.C!ml Manually (Proceed with Caution!)
If you decide to remove malware manually, follow our step-by-step guide below. Note that this process takes 20-30 minutes and requires some technical skills. If you do not follow our steps carefully, this may damage or corrupt your Windows system, and you will end up paying more to reinstall the system and recover your data than getting malware removal software in the first place.
Before Proceeding to Solutions, You Need to Enter a Safe Mode
Step 1. Search for ‘Recovery Options‘ > Recovery > Advanced start-up > Restart now
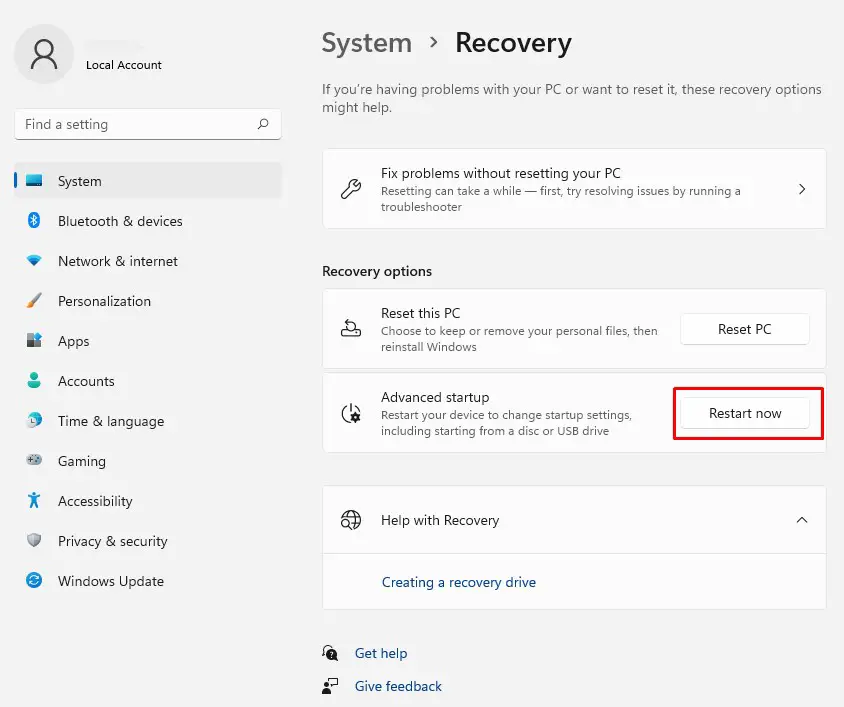
Step 2. Then in Choose an option menu go to Troubleshoot > Advanced options > Startup Settings > Restart
Step 3. Once restarted, select Safe Mode with Networking and press Enter
Now let’s proceed to malware removal steps… Please follow our exact order of solutions to have a higher chance of success.
Solution #1 – Delete Suspicious Tasks in Task Scheduler
Step 1. Go to Control Panel > Administrative Tools > Task Scheduler
Step 2. Open the Task Scheduler Library folder and delete suspicious tasks
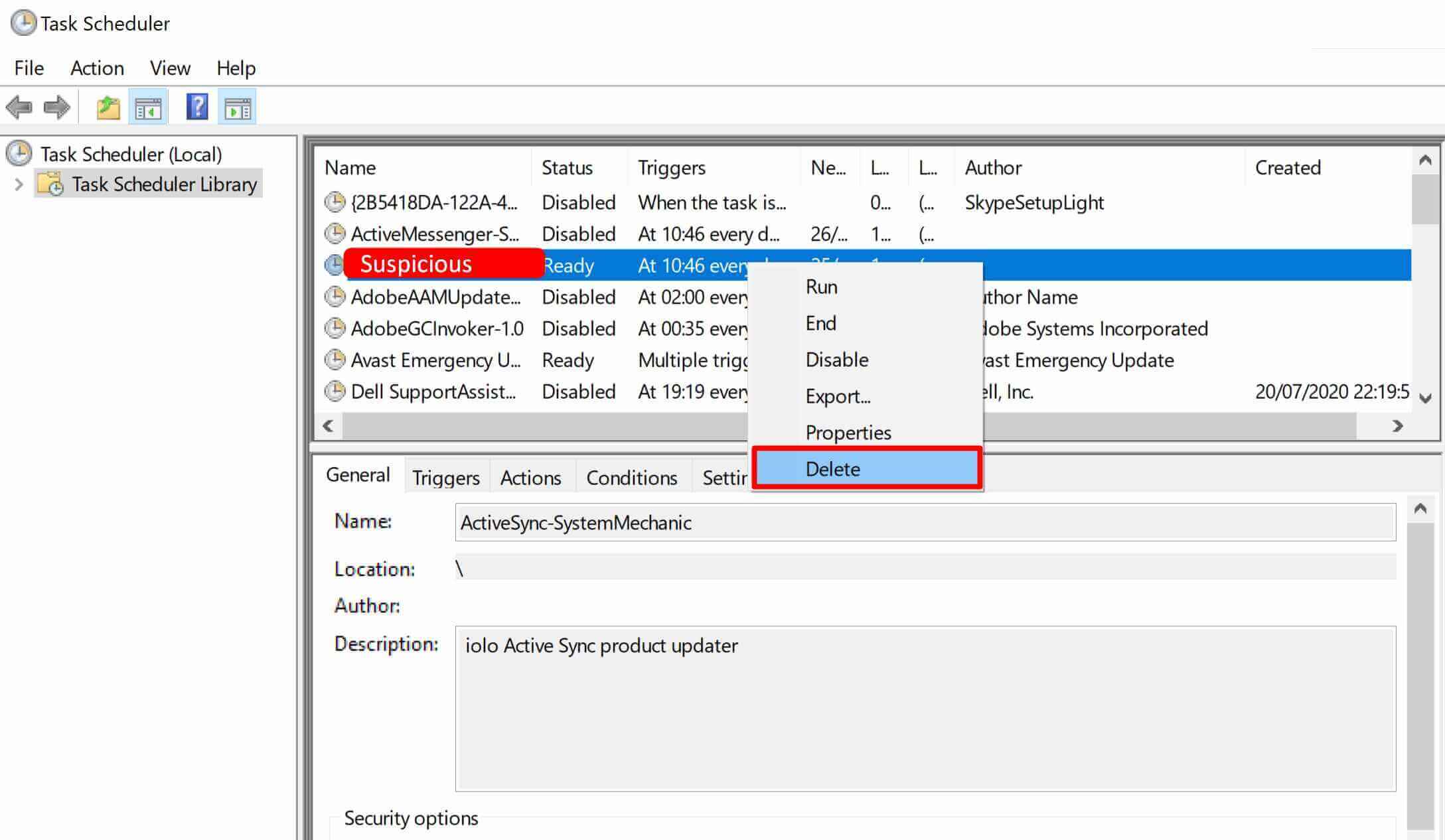
TIP: if you don’t recognize suspicious tasks, filter by ‘Created’ date and check the latest created tasks. Also, suspicious tasks might have a missing Author.
Solution #2 – Delete Suspicious Programs in Programs and Features
Step 1. Go to Control Panel > Programs and Features
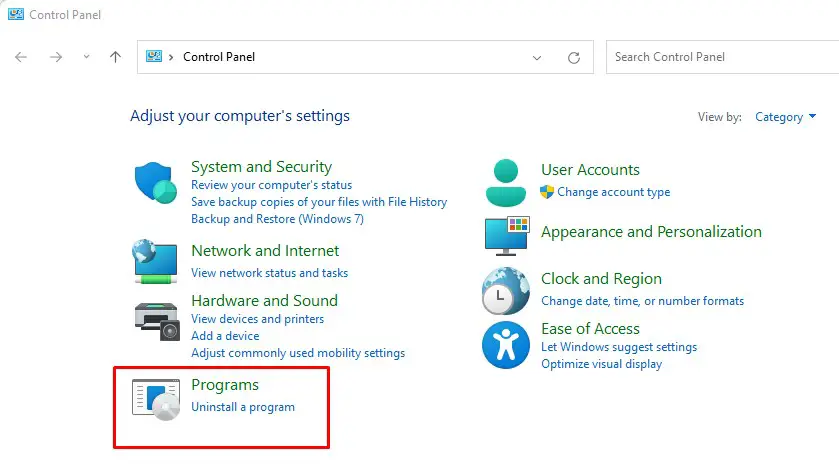
Step 2. Sort by ‘Installed On‘ date and delete suspicious programs
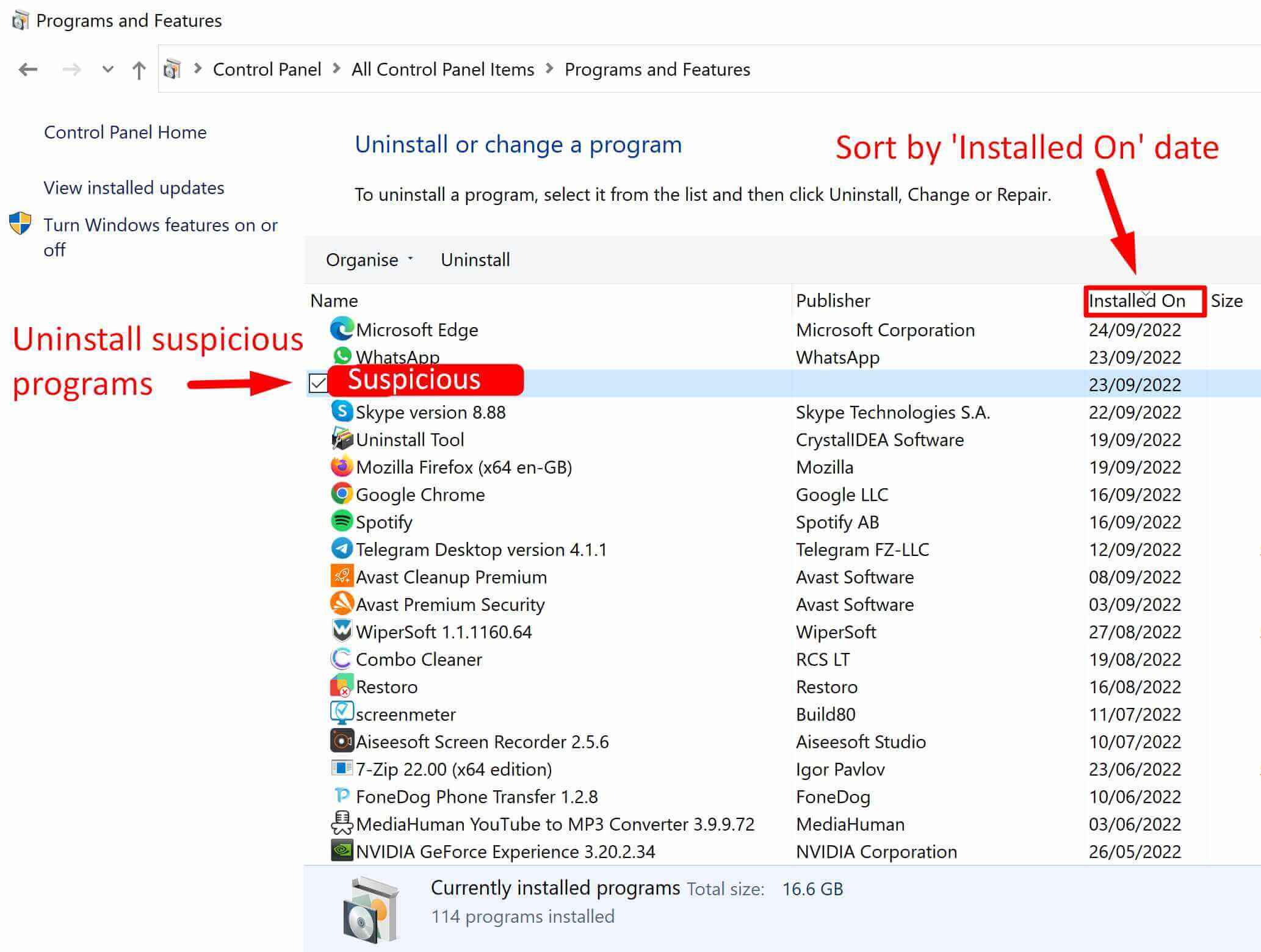
TIP: Think about what programs were installed just before your PC got infected.
Solution #3 – Delete Suspicious Files from Task Manager
Step 1. Open Task Manager and go to the Details tab
Step 2. Search for suspicious processes
Step 3. Right-click on suspicious process > Open file location, and delete the file or whole folder
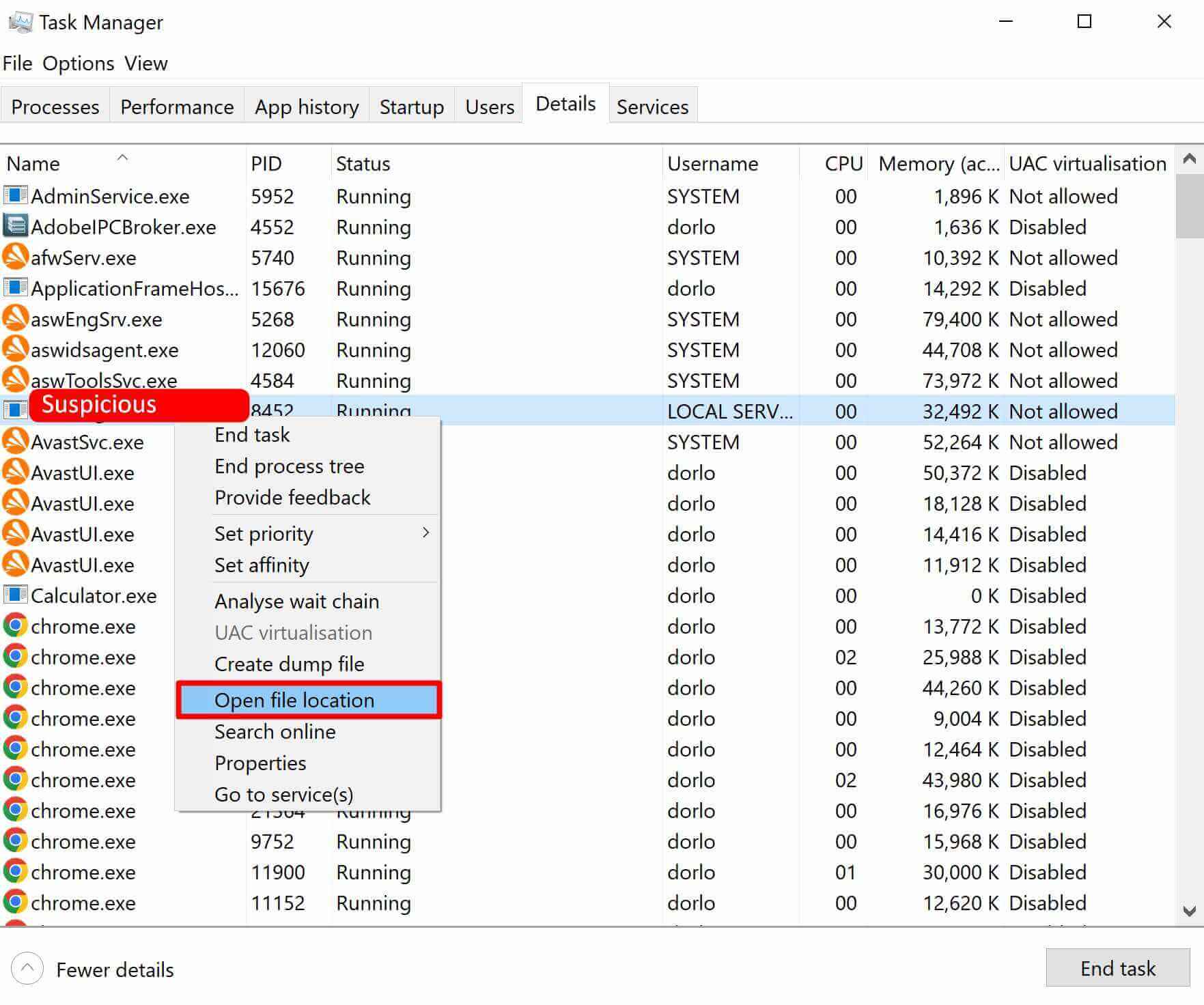
Step 4. Get back to Task Manager and end the suspicious process
Step 5. Then search the Startup tab for suspicious processes > Open the file location, and delete the file or whole folder
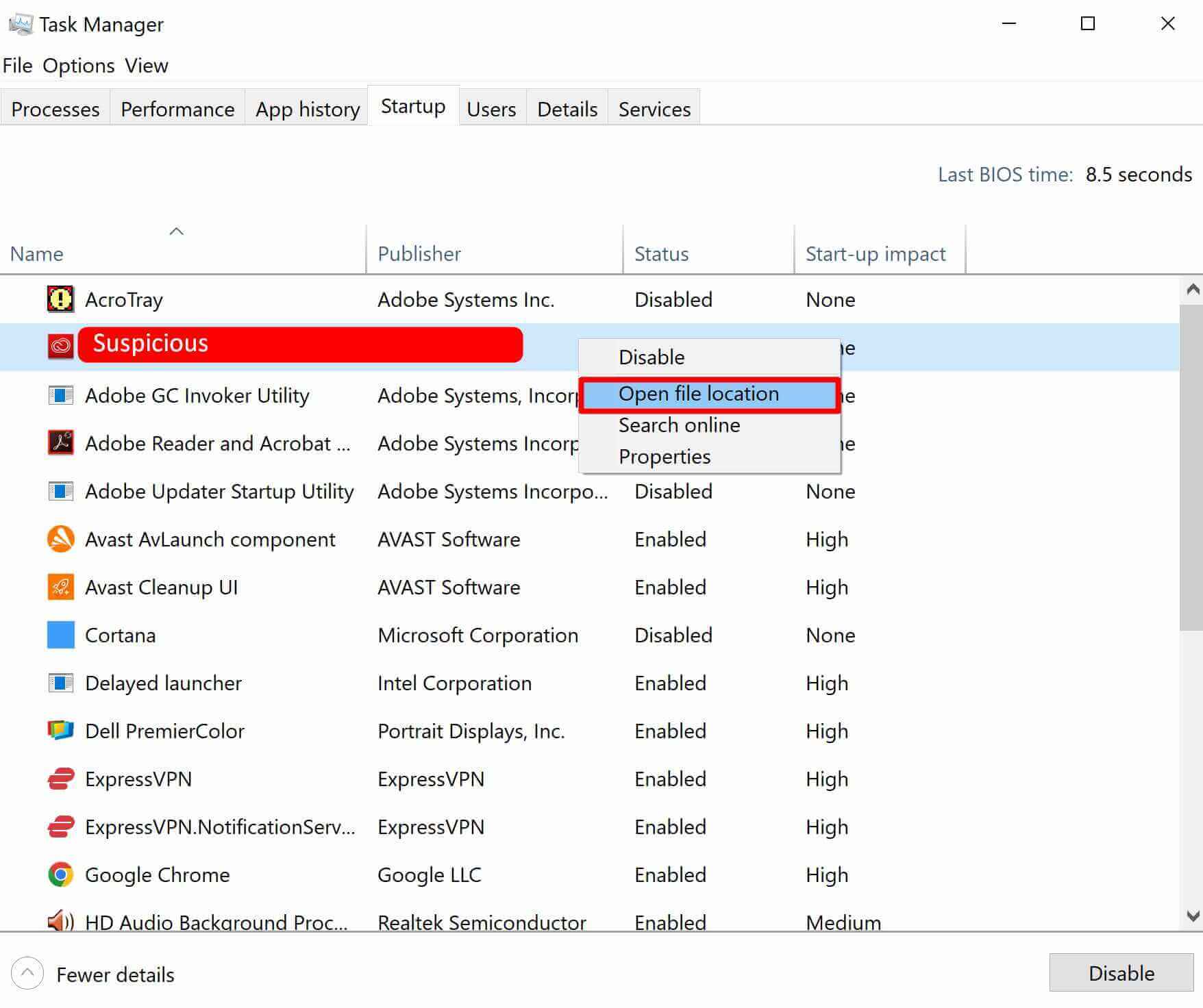
TIP: If ‘Access is denied’ and you’re unable to delete files, search for Resource Monitor (run as administrator), open and end the process in the Overview tab, then try to delete a file.
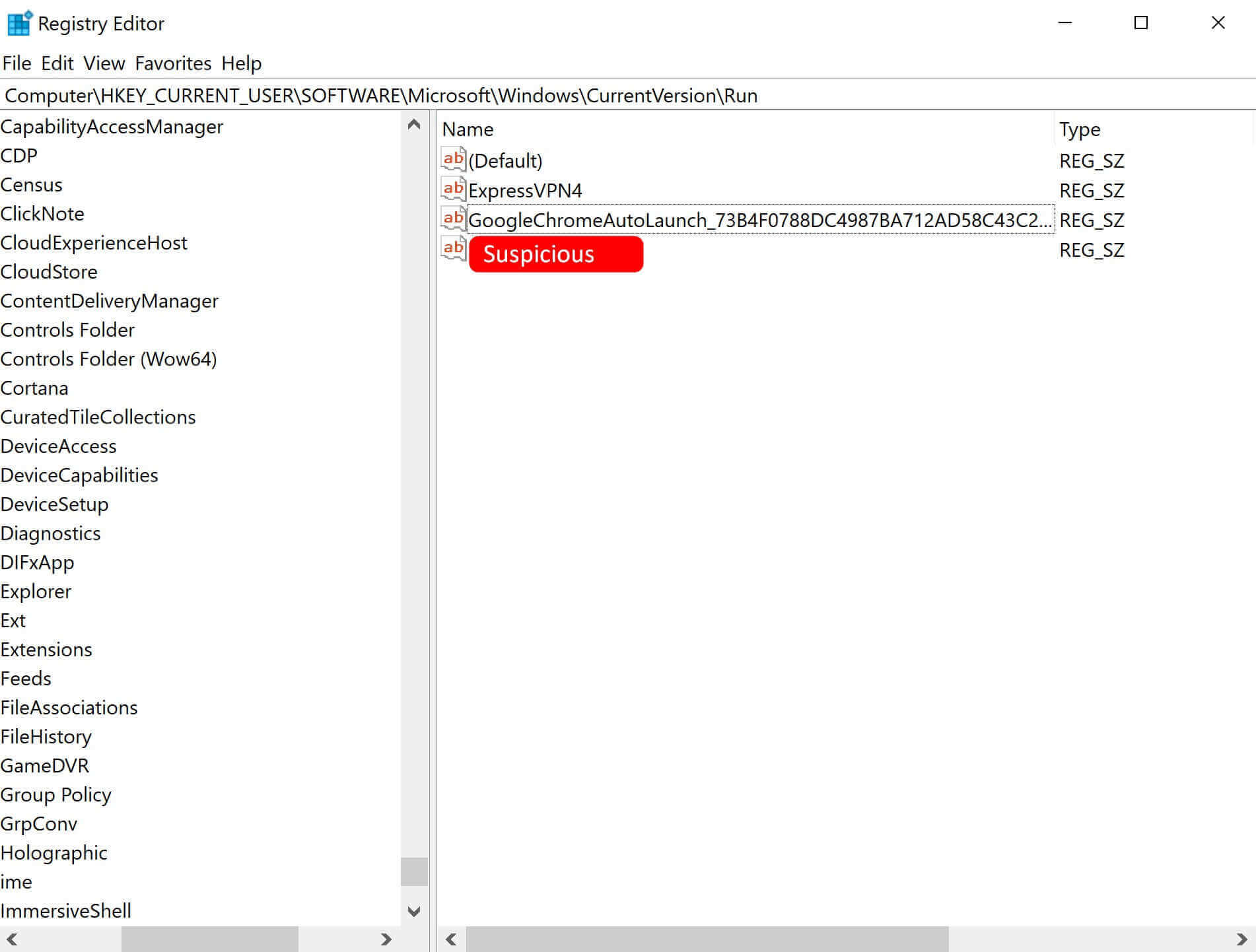
Solution #4 – Delete Suspicious Registries from Registry Editor
Step 1. Open Registry Editor (Run as administrator)
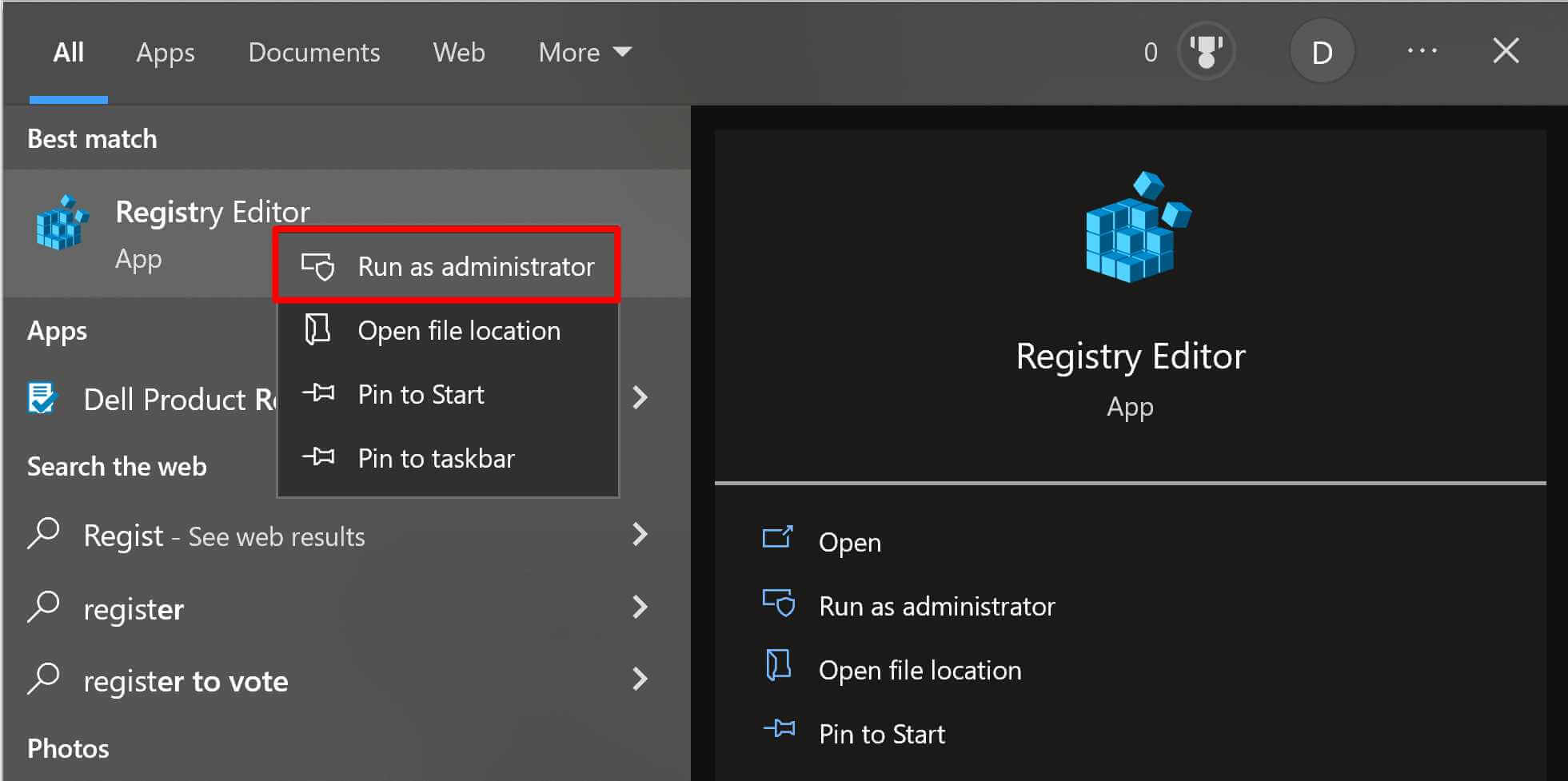
Step 2. Delete suspicious registries from:
ComputerHKEY_CURRENT_USERSOFTWAREMicrosoftWindowsCurrentVersionRun
ComputerHKEY_CURRENT_USERSOFTWAREMicrosoftWindowsCurrentVersionRunOnce locations
Step 3. Then select Computer and go to Edit > Find, and search Registry by names of suspicious files you remember from previous steps
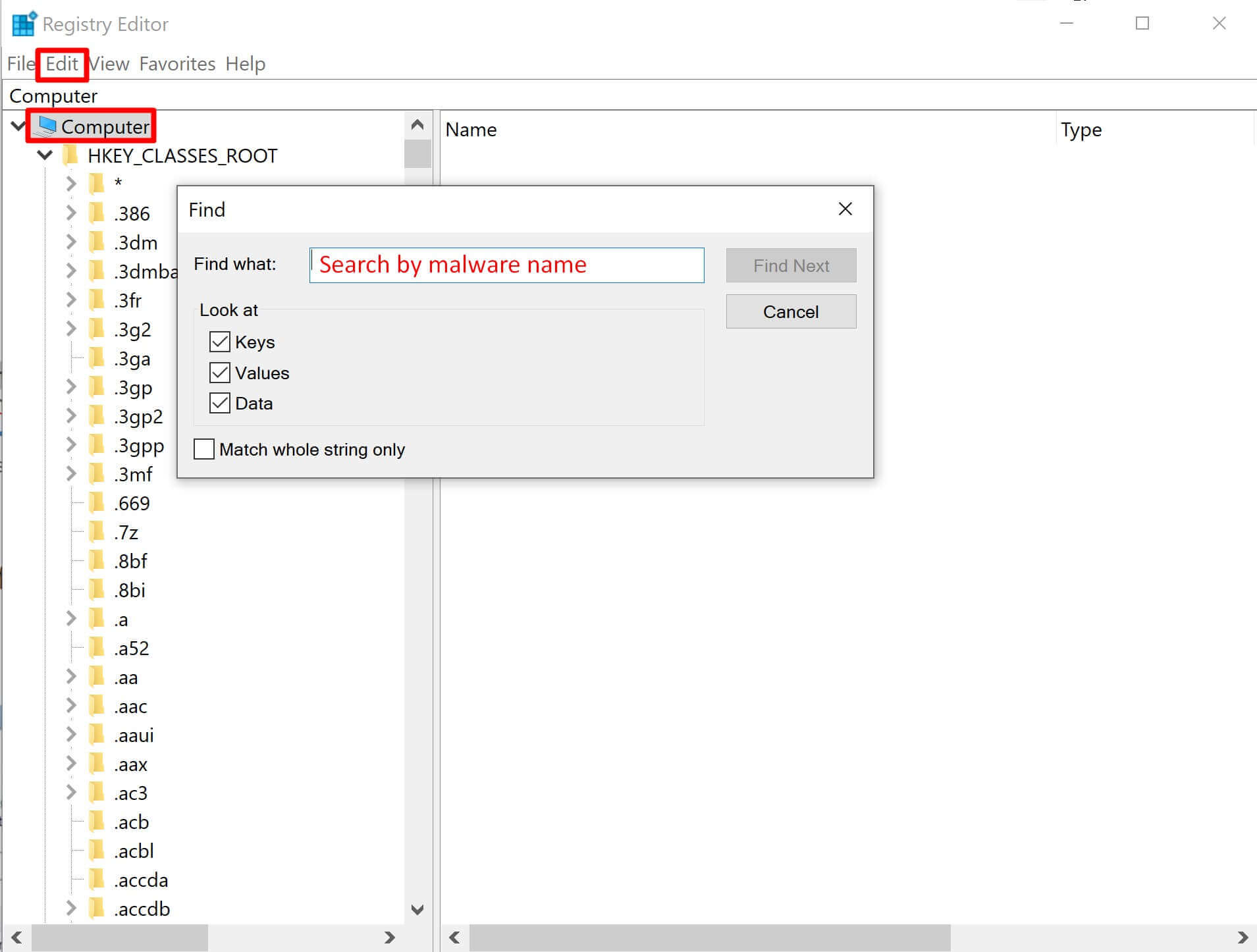
TIP: You can easily delete suspicious registries from Run and RunOnce folders, however, be careful with deleting registries from other folders. This can break your system.
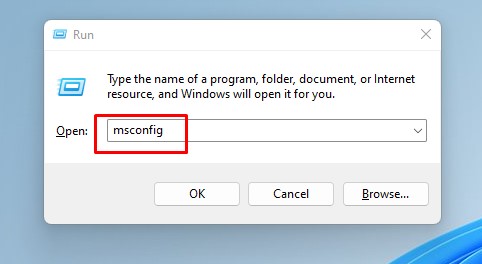
Solution #5 – Disable Suspicious Services in System Configuration
Step 1. Search for Run and type msconfig, then open the Services tab
Step 2. Tick ‘Hide all Microsoft services‘
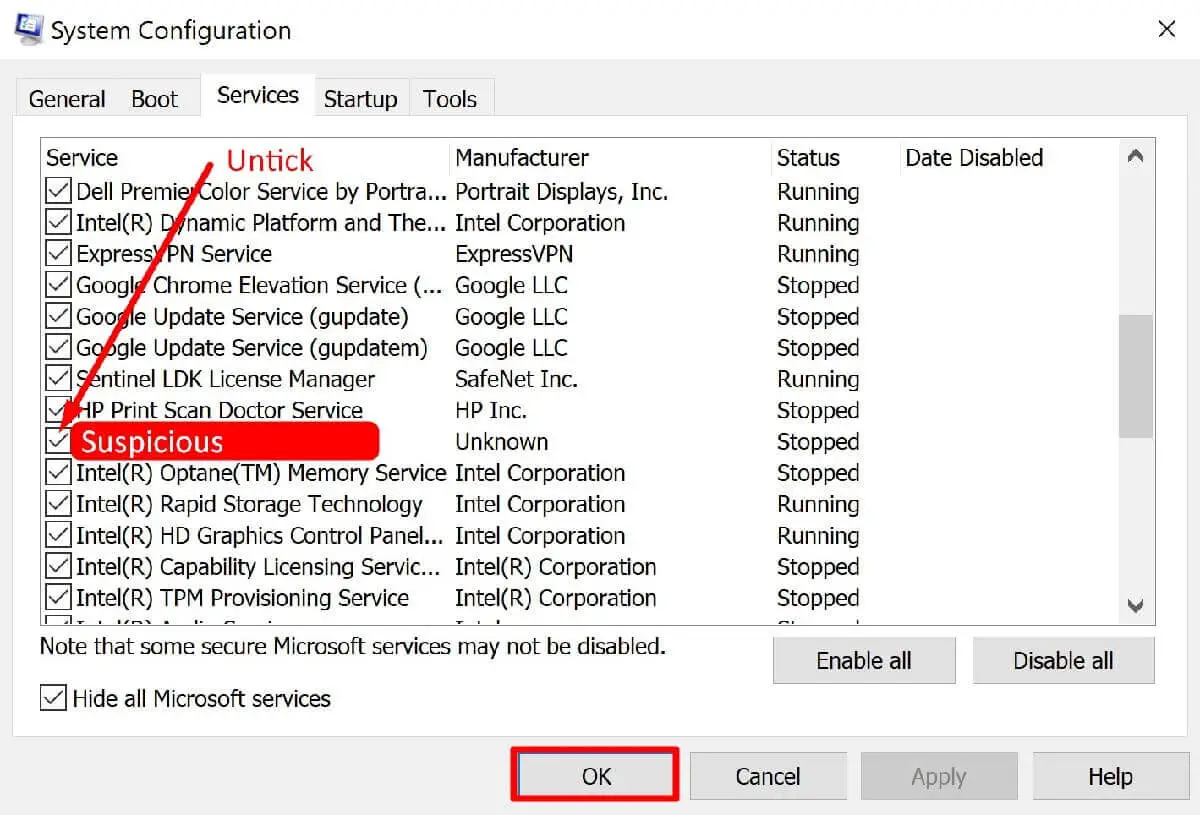
Step 3. Then search a list for suspicious services and untick them
TIP: Missing or unknown Manufacturer can be a good sign of suspicious service
Solution #6 – Delete Temporarily Files
Step 1. Search for Run and type %temp%
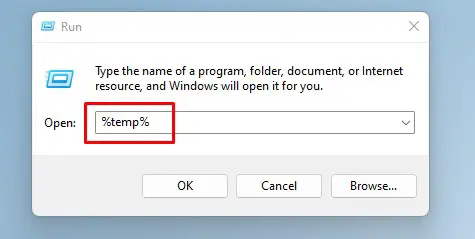
Step 2. Delete everything in the Temp folder
Step 3. Empty Recycle Bin
TIP: all temporary files can be deleted without hesitation. It will not damage your system.
Solution #7 – Check Hosts File
Step 1. Go to C:WindowsSystem32driversetc, and open the hosts file as Notepad
Step 2. Delete everything below ‘# ::1 localhost‘
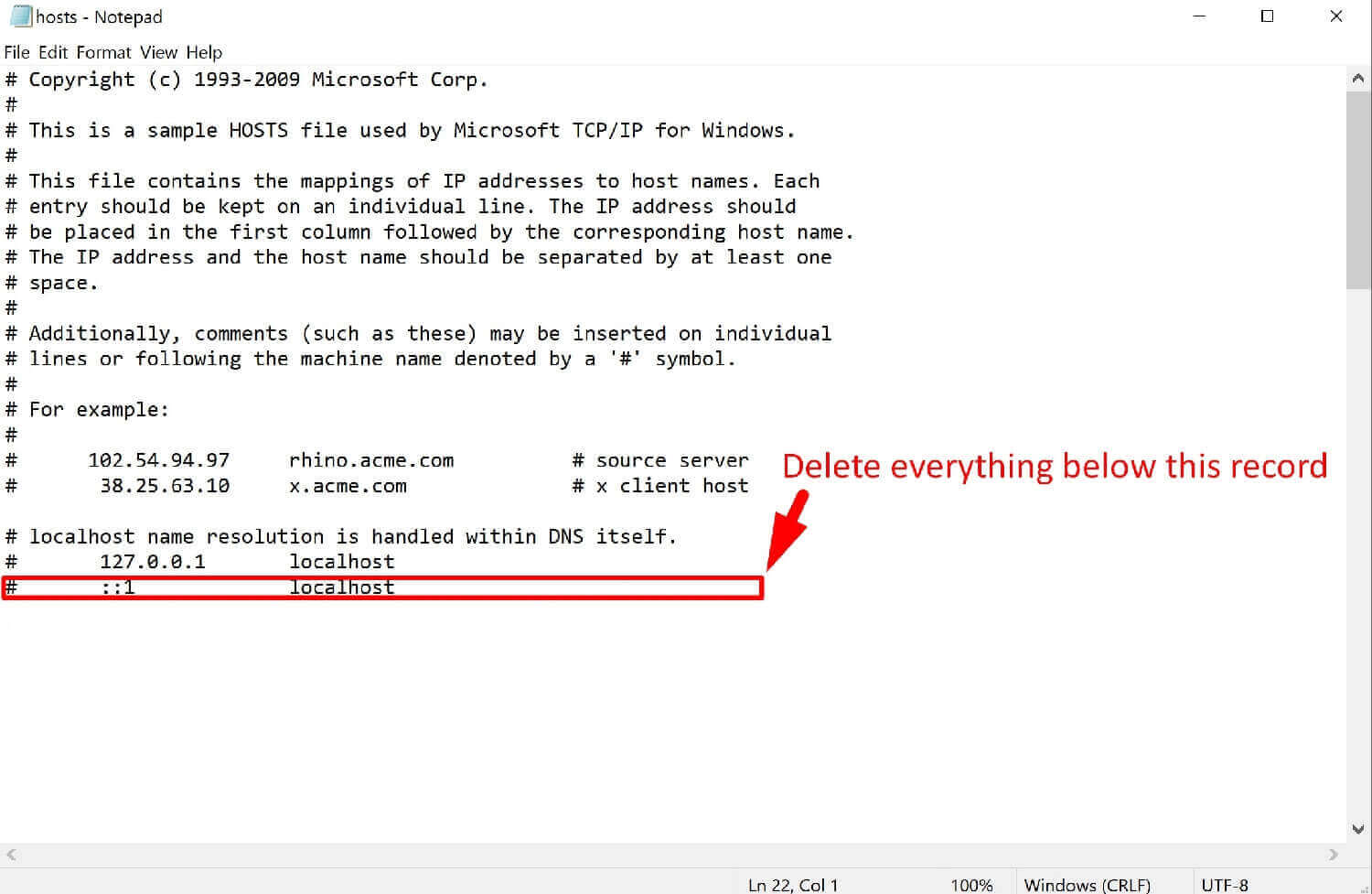
TIP: If a record doesn’t have ‘#’, this is definitely a suspicious record that should be deleted.
Solution #8 – Clean Browsers
Step 1. Search for your browser, right-click and open file location
Step 2. Then right-click on the browser icon and open Properties
Step 3. Delete everything after exe” in Target (for example, Google Chrome’s target should end with chrome.exe”)
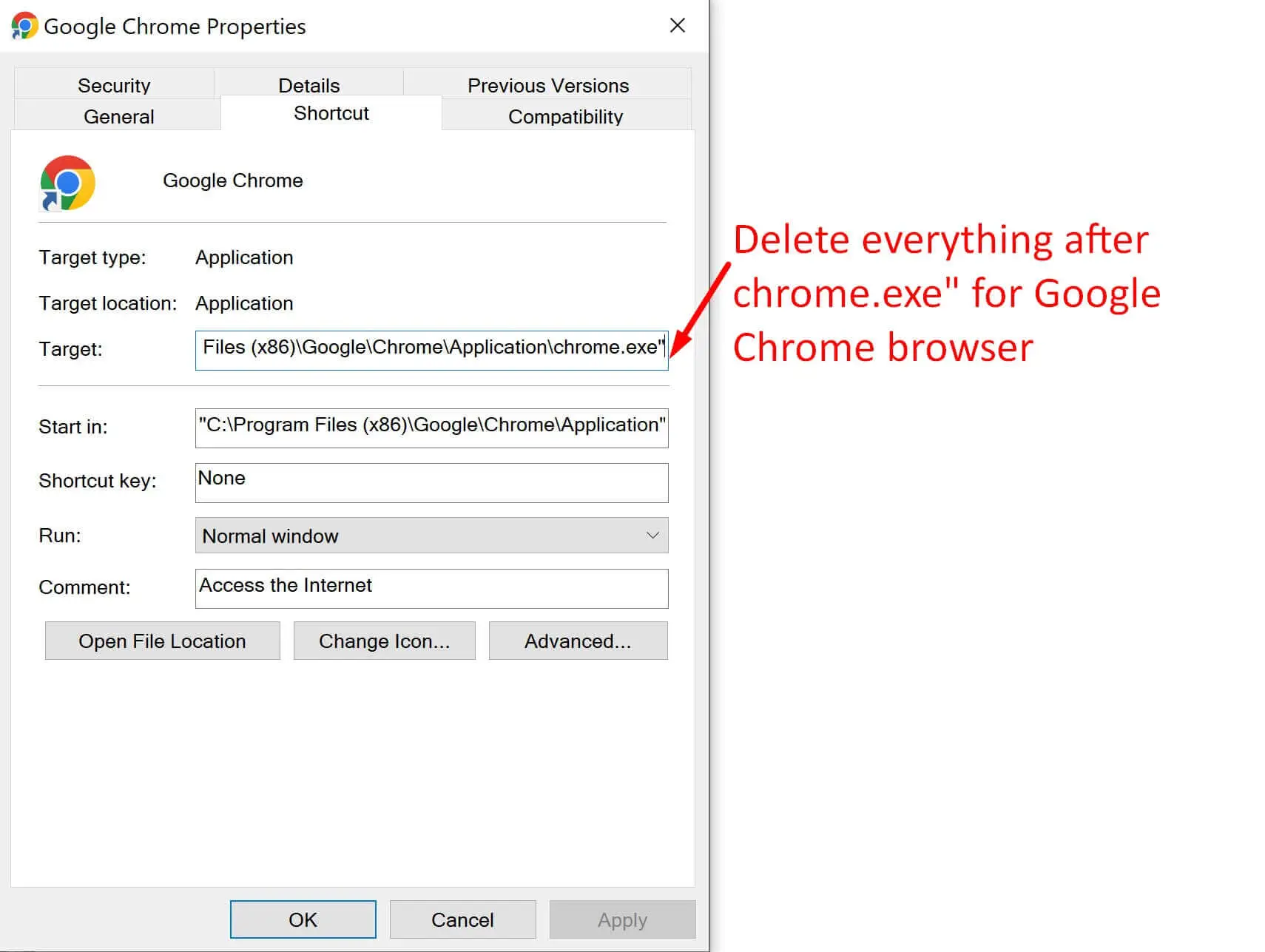
Then you need to open your browser, delete suspicious extensions, notifications, and reset settings to defaults.
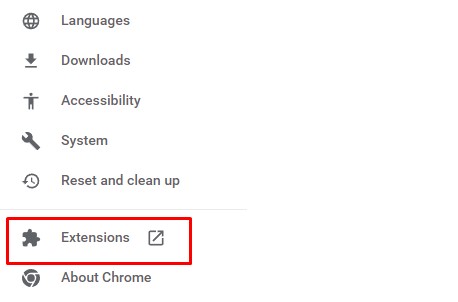
• Google Chrome:
Delete suspicious extensions: Settings > Extensions
Remove suspicious notifications: Settings > Privacy and security > Notifications, then remove suspicious notifications under ‘Allowed to send notifications‘
Reset settings to defaults: Settings > Reset and clean up > Restore settings to their original defaults > Reset settings
• Mozilla Firefox:
Delete suspicious add-ons: Menu > Add-ons and themes
Remove suspicious notifications: Menu > Privacy & Security > Notifications > Settings…, then remove websites you do not want to receive notifications from
Reset settings to defaults: Menu > Help > More troubleshooting information > Refresh Firefox > Refresh Firefox
• Opera:
Delete suspicious extensions: Click on Opera icon > Extensions > Extensions
Remove suspicious notifications: Click on Opera icon > Settings > Advanced > Privacy & security > Site Settings > Notifications, then under ‘Allowed to send notifications’ remove websites you do not want to receive notifications from
Reset settings to defaults: Click on Opera icon > Update and recovery > Recover
• Microsoft Edge:
Delete suspicious extensions: Menu > Extensions
Remove suspicious notifications: Menu > Settings > Cookies and site permissions > Notifications, then under ‘Allow‘ remove websites you do not want to receive notifications from
Reset settings to defaults: Menu > Settings > Reset settings > Restore settings to their default values > Reset
Solution #9 (Optional) – Follow This Solution if Your Browser Does Not Open Any Websites
If your browsers do not open any websites while other software can connect to the internet properly, you need to check internet properties:
Step 1. Go to Control Panel > Internet Options > Connections > LAN settings
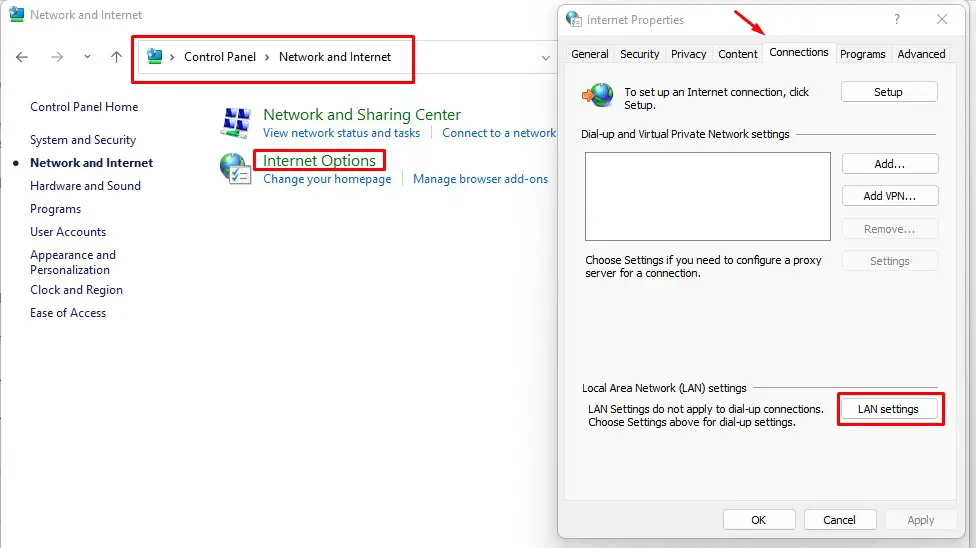
Step 2. Tick ‘Automatically detect settings’ and untick ‘Use a proxy server for your LAN’
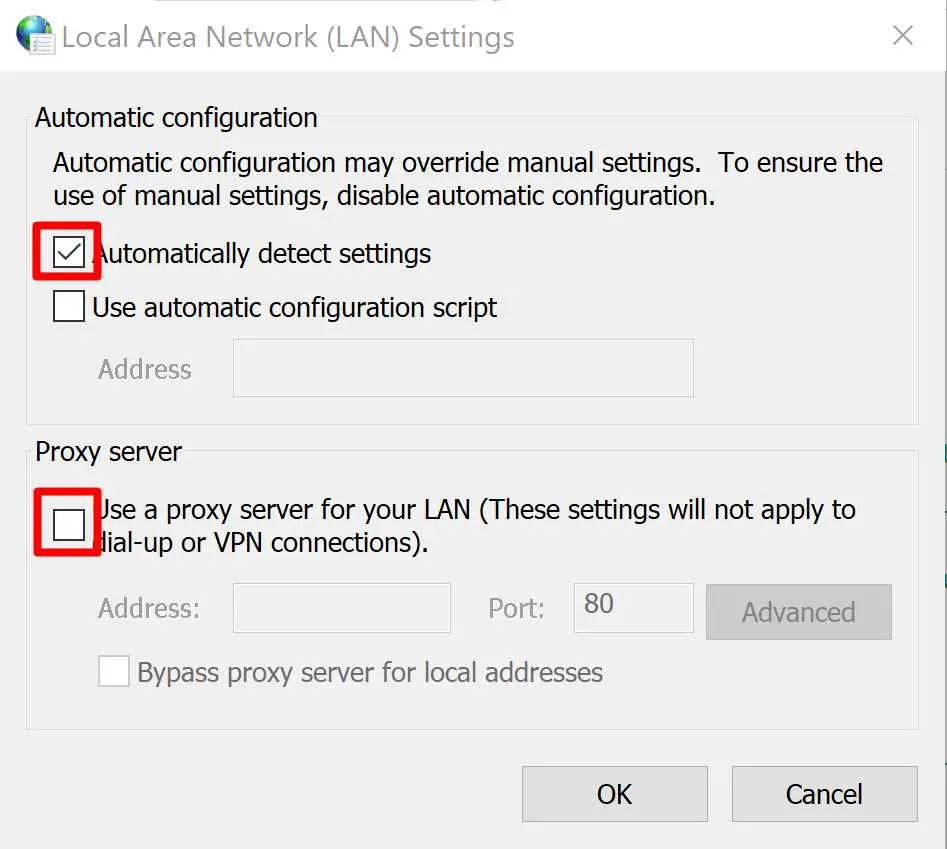
Step 3. Then disable proxy servers in the browser if connection wasn’t restored yet
• Check AppInit_DLL in Registry
Step 1. Open Registry Editor (Run as administrator)
Step 2. Go to Edit > Find, search for AppInit_DLLs
Step 3. Open the AppInit_DLLs file and make sure Value Data is empty (don’t remove records starting with “SYS:”)
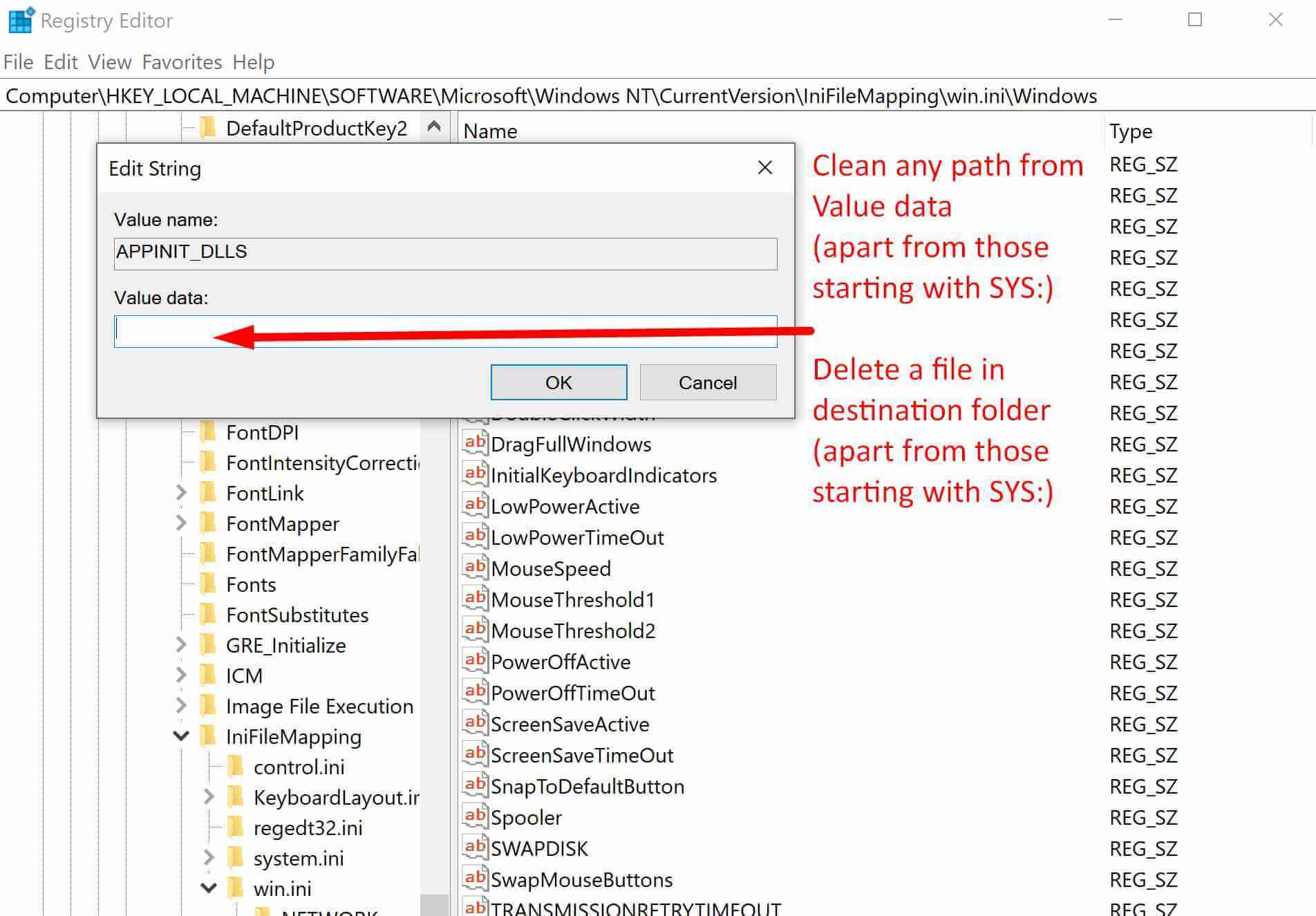
Step 4. If Value Data contains a path to any DLL file, follow that path, find and delete that DLL file, and clean Value Data in AppInit_DLLs file.
TIP: DLL file may be hidden in the destination folder. In that case, change the folder setting by going to View > Options > Change folder and search options > View, then select ‘Show hidden files, folders and drives’
• Check DNS servers
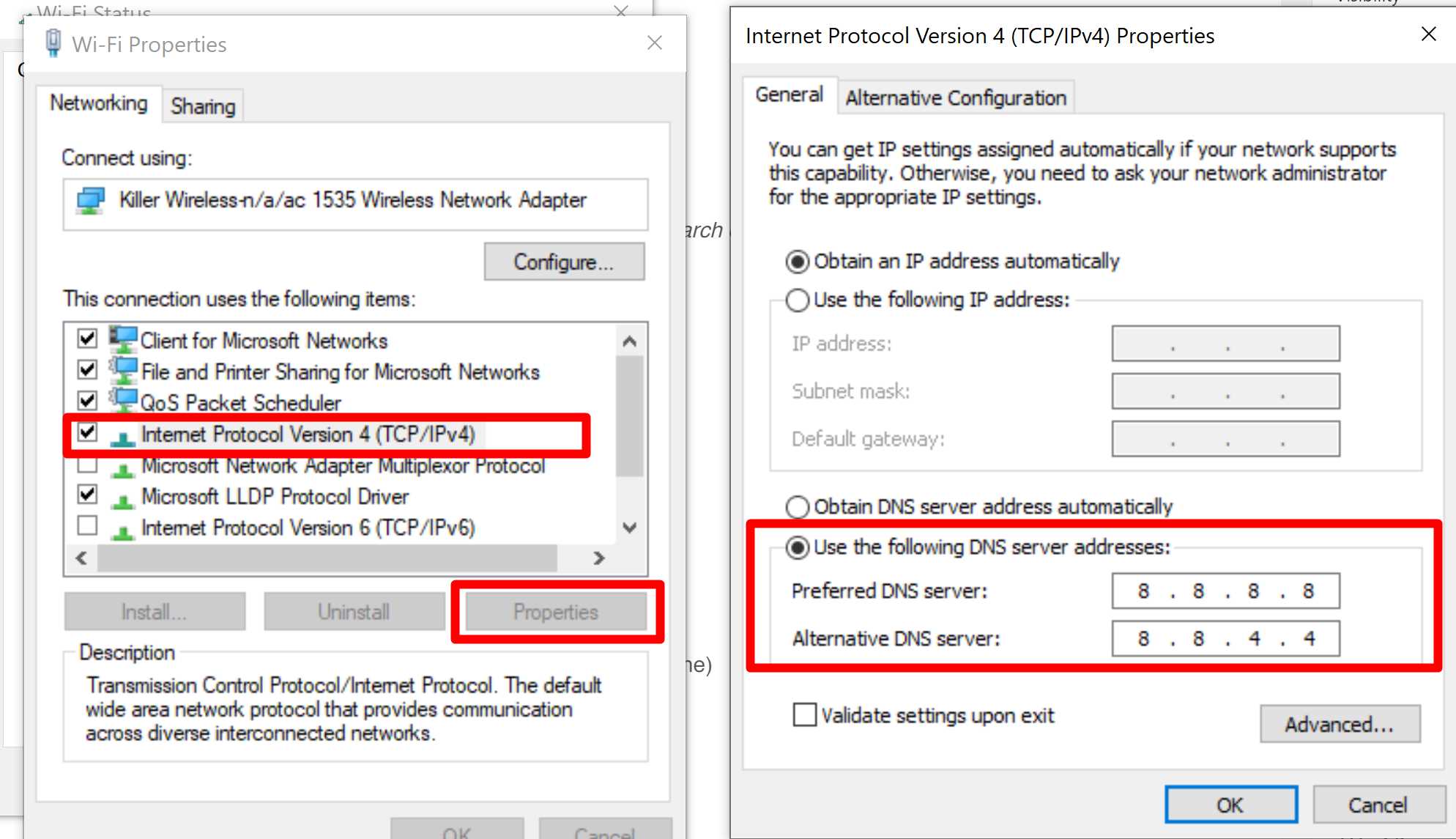
Step 1. Go to Control Panel > All Control Panel Items > Network and Sharing Centre, then click on your Connection
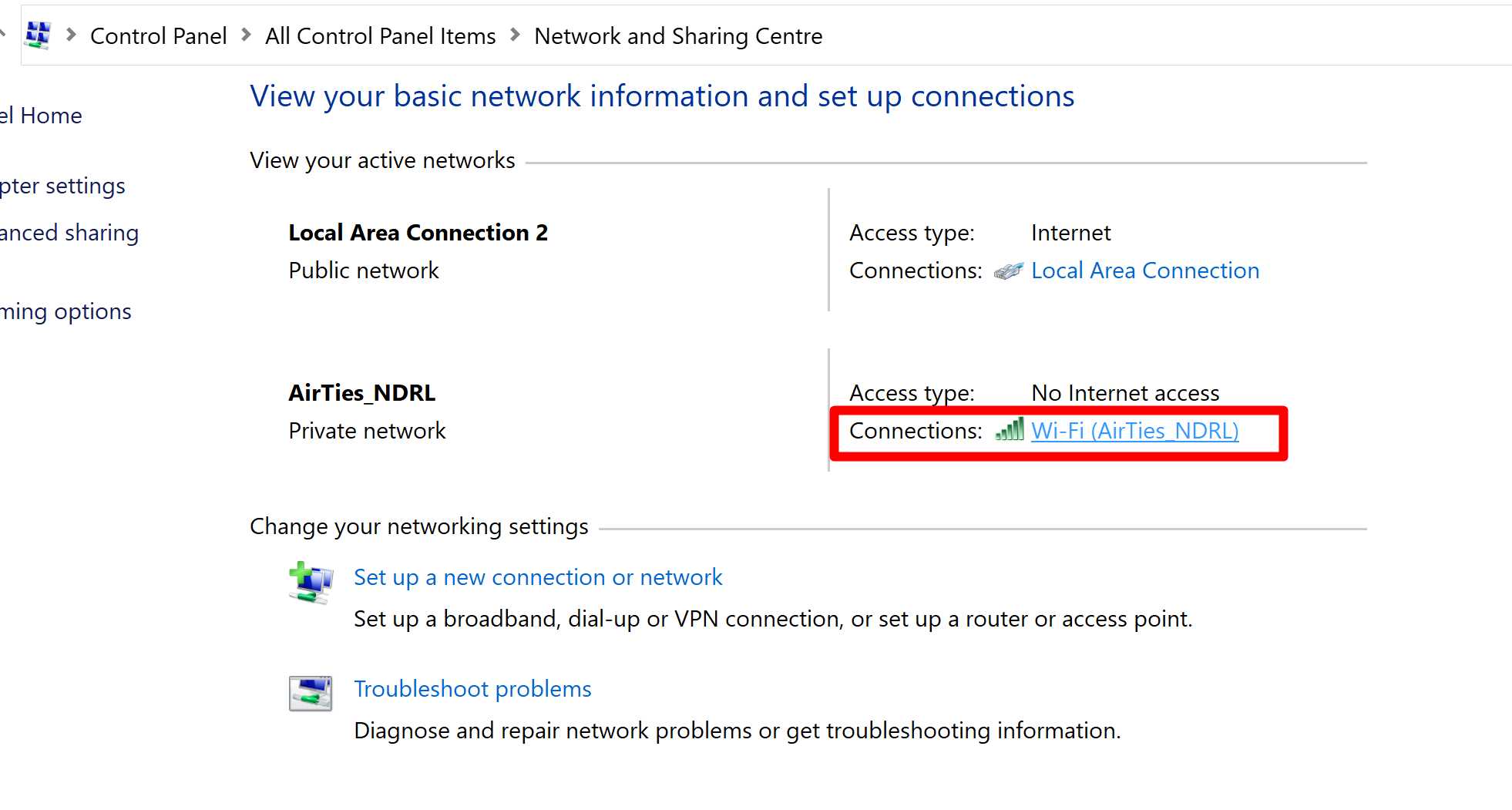
Step 2. Open Properties > Internet Protocol Version 4 (TCP/IPv4)
Step 3. Select ‘Use the following DNS server addresses’ and enter 8.8.8.8 to Preferred DNS server and 8.8.4.4 to Alternative DNS server
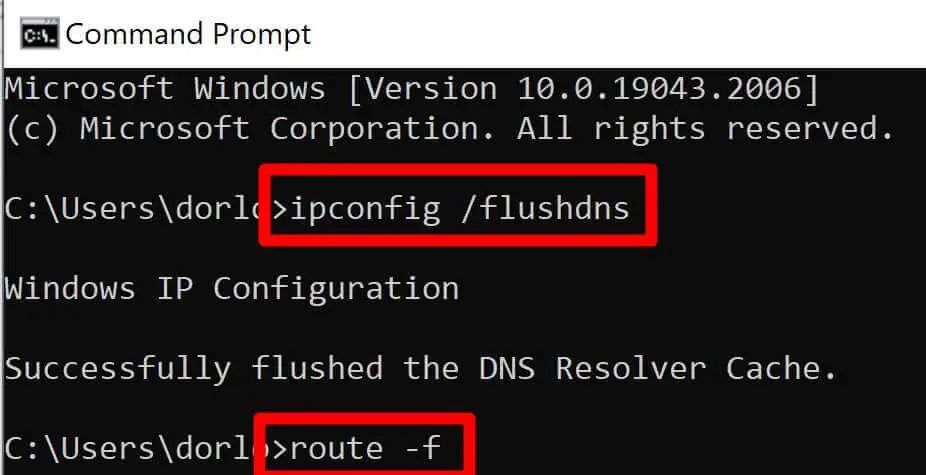
Step 4. Then open Command Prompt and enter the following commands: ipconfig /flushdns then route –f (these commands will clean DNS cache)
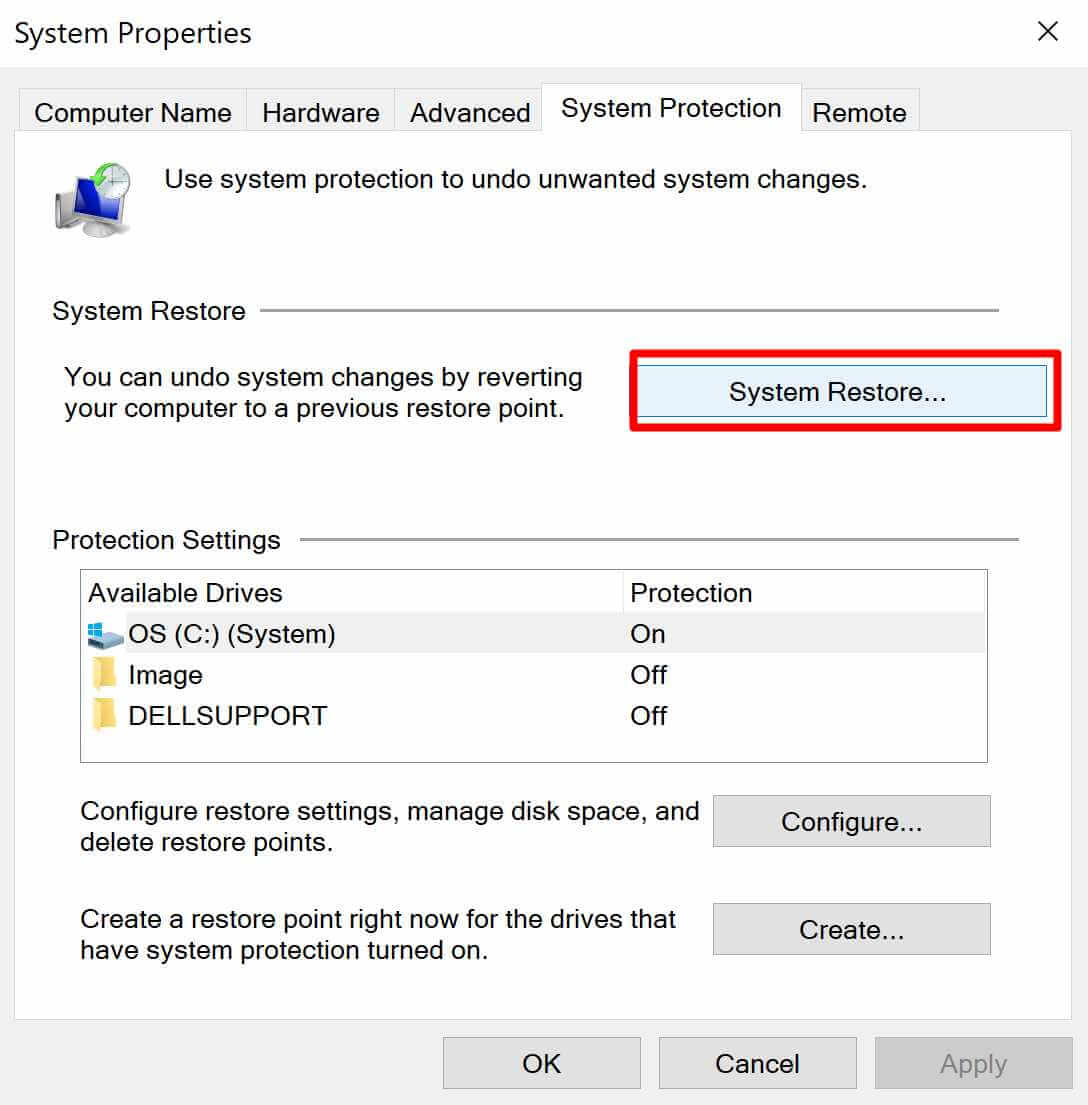
Solution #10 (Optional) – Restore the Windows
If the steps above do not remove malware, you can restore your Windows to the earlier point. This will not affect your pictures, documents or personal data, but some programs or drivers might be uninstalled.
Search for Create a restore point > System Restore… > Next > Select a date you want to restore your system to > Next > Finish
You may also need to decrypt or recover your personal files.
Final Thoughts
The Win32/Wacapew.C!ml is a dangerous trojan you should remove immediately after you notice it on your computer. This article has highlighted automatic and manual ways to remove this virus. We recommend the Spy Hunter software if you want to remove it quickly. It has the necessary features to eliminate this virus.
FAQs
We recommend removing Win32/Wacapew.C!ml with Spy Hunter or following our manual malware removal guide in this article.
There are several ways this virus infects one’s computer. They include web injectors, malicious software programs, social engineering attacks, dubious advertisements, etc.




![How to Remove jsagent-egf [adw] Virus (Tested Solutions)](https://tentechreview.com/wp-content/uploads/2022/10/How-to-Remove-jsagent-egf-adw-Virus-Tested-Solutions-350x250.jpg)





![How to Take a Screenshot on Samsung Galaxy Nexus I9250 [+ Video Guide]](https://tentechreview.com/wp-content/uploads/2022/01/Take_Screenshot_Samsung_Galaxy_Nexus_I9250-2-120x86.jpg)
![How to Take a Screenshot on Huawei P8 [+ Video Guide]](https://tentechreview.com/wp-content/uploads/2022/02/Take_Screenshot_Huawei_P8-9-120x86.jpg)
![How to Take a Screenshot on Samsung Galaxy C9 Pro [+ Video Guide]](https://tentechreview.com/wp-content/uploads/2022/01/Take_Screenshot_Samsung_Galaxy_C9_Pro-3-120x86.jpg)
![How to Take a Screenshot on Samsung Galaxy A8+ (2018) [+ Video Guide]](https://tentechreview.com/wp-content/uploads/2022/01/Take_Screenshot_Samsung_Galaxy_A8_2018-120x86.jpg)

![How to Take a Screenshot on Samsung Galaxy Y Pro B5510 [+ Video Guide]](https://tentechreview.com/wp-content/uploads/2022/01/Take_Screenshot_Samsung_Galaxy_Y_Pro_B5510-1-120x86.jpg)
